Hacking and piracy of your website what hackers do really want?
If you use a modern content management system (CMS like WordPress), chances are important to see your instance visited by pirates.
Unfortunately, if you are unprepared, the experience may be damaging to your online reputation. In all cases, it is painful for your domain name and your visitors.
What do want those pirates?
Unless your website or your organisation has a particular brand, there is a tiny risk that you undergo a type of “defacing” attack. It represents a quarter of the sites attacked.
A “defacing” attack aims to replace your homepage with a message like “Marcel Anonymous passed here“. It could be provocative and display a claim related to the theme of your organisation. Or sometimes your attackers only want to cut your website for various reasons.
What are doing the attackers of a website?
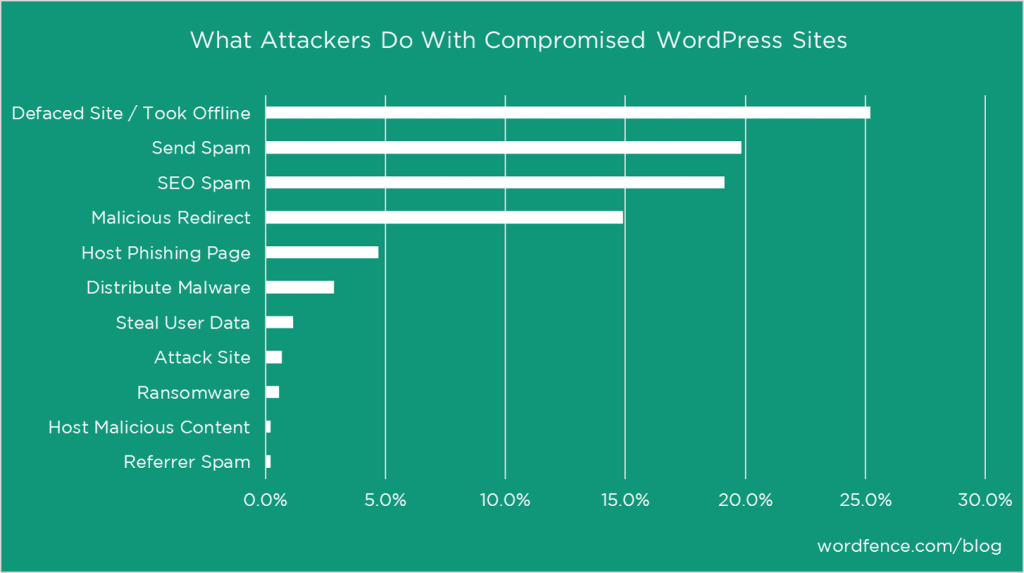
The vast majority of attacks is to be able to use your resources:
- the power of your server
- and authority of your pages in Google rankings.
Rodeo-Hacking
Hackers want to enjoy as long as possible from your space. It’s part of a rodeo-hacking: it must stay online as long as possible.
The majority of scripts from hackers are useful to:
- generate spam actions (massive sending of pornographic or pharmaceutical emails)
- to serve for DDOS attacks (they flood servers with traffic to put them down),
- generate fake traffic to some sites (the majority of ad brokers are using it),
- to capture your visitors’ browsers to make them perform actions without their knowledge (e.g., your browser realizes clicks on advertisements on other websites, insert messages on FB by hacking the profiles of your visitors or clicks on links in Google results)
- … (Unlimited imagination)
A real web server can send 60 to 100.000.000 spams in one day. Yes : 100 millions of emails sent in one day from your webserver.
Imagine you discover the intrusion 90 days later. This invasion sent between 5.4 to 9 billion spam emails. Bam !
If emails are using the header of your domain, there is a safe bet that your email will be blacklisted on different quality email services. So your entire enterprise can suffer because your emails will arrive in spam boxes.
How a hacker does manage to get on your website?
In this video, made by a security consultant, you have an illustration of an application “shell” that can load thirty applications of attacks. They will try to enter through the doors, windows, roof or the basement of your website.
Take the time to watch the first minutes; you’ll be surprised by the speed which he directed the intrusion.
The invisible wound of mini-sites
Mini-sites, mostly created in static pages, settled in the heart of your website. They are located in inaccessible folders from your navigation. They are here incognito (for you).
The primary strategy of theses fake sites is to create a useful reserve of pages to create links to other marketable websites.
In this case, hackers are not interested in your visitors’ trafic. They will never see these pages. But search engines, themselves, find hidden links in your navigation or links from other spammy websites. Arrived on these “dummy” pages, they will follow outgoing links.
By manipulating the Google algorithm, these pirates manage to create networks of thousands of shadow websites. They connect hundreds of thousands or even millions of pages.
Imagine a failure on a CMS plugin installed on 500,000 websites. 100,000 websites are infected before the security update.
Take for example an installation of 2 mini-sites ( 100 pages ) on each infected sites.
Bingo! You have 20.000.000 of pages available. It just takes two days. So imagine the pace of their network when they have hundreds of bots that are attacking websites everyday.
This “invisible network” makes a false popularity to sites they want to promote. Enabling them to achieve excellent rankings in the results of Google (and other engines).
Your site is your asset. It is there since several years. You have produced hundreds or even thousands of pages. You get “clean” links from trusted sites. You never say “natural” links because they are never “natural” in the google’s eyes.
It is, therefore, tough for Google to discover the swindle.
At least quickly.
And when the “pot aux roses” is discovered then your domain is penalized by Google. Your site may simply be downgraded from its indexes suffering a manual penalty.
Hackers do not care: you are a lost among hundreds of thousands. One in a million.
The bad news: those nasty backlinks aiming to your domain
The Pirates used their “canvas” to send you hundreds of weak links to pages hidden in the heart of your website.
They need to create a “false popularity” for those pages which in turn influence other pages elsewhere. Small rivers make noise.
Once neutralized the attack on your server, you will have erased the pages of mini-sites. But the bad backlinks still point to your site. Even generating 404 errors, they are still aiming your domain. And this “bad reputation” will be very damaging if you do not act firmly to clean that mess.
Thus begins your journey of repentance (even if you are not responsible): a long process of cleaning and clemency requests near Google God’s employees responsible for verifying your efforts.
It is not unusual to wait three to six months before returning into the rankings on the queries that you covet.
Photo credit: mibuchat